Latest Whitepapers

Centrify Zero Trust Privilege and Password Vaults
Privileged Identity Management (PIM) solutions are based on a variety of fundamental technologies, with...

Fortinet Federal Government Cybersecurity Solutions
U.S. federal agencies operate some of the world's largest and most complex digital networks, but many...

SASE-Ready WAN Edge for the Work from Anywhere Era
Enterprise networks are on the verge of a major tipping point, driven by the shift from employees working...

Why automation is essential for cyber resilience
Digital transformation makes today's businesses more productive and more vulnerable to cyberattacks....

Data Management in a Multi-Cloud World: Finance and Insurance Edition
This report focuses on a recent quantitative research study conducted with UK and Ireland IT decision...

Digital Marketing Transformed: The future of content
Digital marketing is, by its very nature, a dynamic place to be. We've seen an explosion in the amount...

The Pitfalls of SASE Vendor Selection: Features vs. Strategic Outcomes
After speaking with 1000s of IT pros, we've learned that success with SASE is only achieved when it meets...

Practical Guide To A Zero Trust Implementation
Zero Trust is becoming the security model of choice for enterprises and governments alike. However, security...
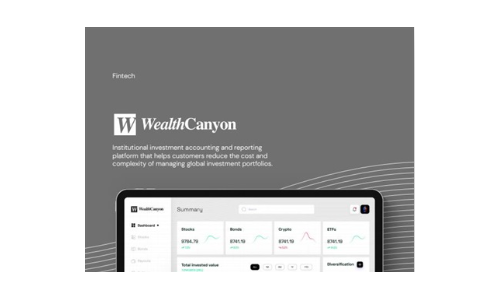
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...
Tracking Bot Trends for first half 2020
Recent bot trends you need to know: Bots can harm an Internet property in a variety of ways and cause...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









