Latest Whitepapers
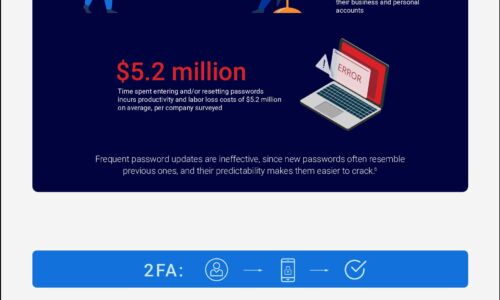
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

10 Ways to Fortify Ransomware Recovery Defenses
Ransomware has become a 'cyber-pandemic' that shows no signs of diminishing anytime soon. Your ransomware...

Keeping Critical Patients Safe and Treated Using SD-WAN
MD Anderson Cancer Center leveraged VMware SD-WAN to help radiologists be more productive, and staff...

Advance Your Ransomware Defenses
Ransomware isn't new. In fact, it's 30-years-old . What IS new is ransomware's sudden rise as a favored...

Stopping BEC and EAC
Business email compromise (BEC) and email account compromise (EAC) are complex problems that require...

The Total Economic Impact™ Of VMware Carbon Black Cloud
Security and IT teams today are constantly dealing with overly complex and siloed toolsets that can't...

Understanding the Obstacles to WAN Transformation
Network engineering and operations leaders are looking to software-defined wide area networks (SD-WAN)...

VMware NSX Advanced Load Balancer Benchmark Report
Moving from appliance-based load balancers to software-defined VMware NSX Advanced Load Balancers could...

Case Study – JUSTWork
JUSTWork wants to invigorate the concept of the workplace. For that to be possible, JUSTWork needs an...

Cloud Report: Cloud Services
In this Netskope Cloud Report™, we've compiled the most interesting trends on cloud service and web...

Top 10 Active Directory Security Reports and Alerts You Need
Traditional perimeter defense is simply no longer good enough. Today, identity is the new perimeter —...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








