IT Management

7 Steps To Get Started with Microsoft Azure
Ready to start using Microsoft® Azure®, but not sure how to get started? Good news: Getting started...

Delivering Secure Financial Services for Your Customers in the Cloud
How financial firms build stellar experiences in the cloud From ordering takeout on an app to joining...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...

The Forrester Wave™: DDoS Mitigation Solutions, Q1 2021
Cloudflare Named A 'Leader' in The Forrester Wave™: DDoS Mitigation Solutions, Q1 2021 Forrester Research,...

The Inner Circle Guide to Omnichannel
ContactBabel's Inner Circle Guide to Omnichannel explores the challenges and opportunities of offering...
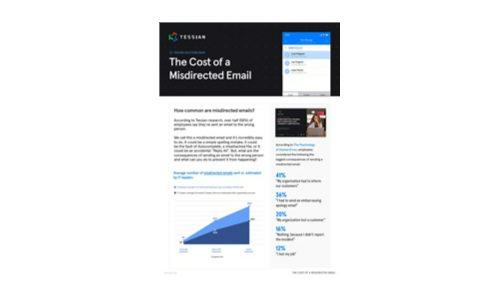
What is the Cost of a Misdirected Email?
The average number of misdirected emails is almost always higher than IT leaders estimate, making it...

Build your future, faster
To support the organization in its pursuit of innovation, and to address future uncertainties, development...

Change management blueprint for contact centre digital transformation
The COVID-19 pandemic put organisational change into hyperdrive. Businesses were compelled to move to...

Secure Access Service Edge (SASE): 7 Ways Your Business Benefits
The benefits that SASE offers organizations helps explain why Gartner estimates that by 2025, 80% of...

Stand out with a winning IT asset management strategy
As professional athletes will tell you, achieving success starts with smart strategies that erase roadblocks...

Achieving Data Excellence in Financial Information Management
Financial institutions have accumulated large quantities of valuable data and metadata, but the levels...

How Proofpoint EFD Is More Than Just DMARC
A raft of solutions have sprung up to help organisations set up and manage their DMARC strategies. Like...

Seven reasons why your enterprise needs intelligent search
Organizations are hungry to use data to grow and improve performance, but enterprises are struggling...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





