IT Management
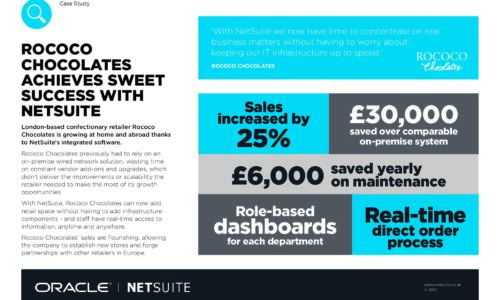
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

Cloud Operations eBook
No matter where you are on your cloud journey, AWS Cloud Operations can help you speed up innovation...

Data In, Value Out
In today's increasingly data-driven business landscape, the companies who succeed are typically those...

The Forrester Wave™: Privileged Identity Management
in our 35-criterion evaluation of privileged identity management (PiM) providers, we identified the 11...

Data Management in a Multicloud World – Finance and Insurance Edition
This report focuses on a recent quantitative research study conducted with UK and Ireland IT decision...

The Total Economic Impact™ Of ServiceNow Field Service Management
ServiceNow® Field Service Management is a cloud-based solution that connects field service to other...

Tanium Risk Assessment: Know Your IT Risk Score
Assess the risk of all your endpoints against multiple vectors — vulnerabilities, threats, compliance,...
Choose the WAF That's Right for You
Despite the industry's best efforts to bolster secure application development practices, the growing...

ESG Distributed Cloud Series Study 2: Cloud-native Applications
IT organizations are trying to keep their businesses running while migrating to modern, future-proof...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









