Internet of Things (IoT)

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

The strategic ROI of network management
ROI for all forms of integrated DNS, DHCP and IP Address Management (DDI) solutions is largely comprised...

5G in the Transport sector
The Transport sector is pioneering the adoption of 5G connectivity, and yet it's doing so with quiet...

Employees are choosing how they work
'The measure of intelligence is the ability to change.' To remain connected, productive and secure in...

8 Business Drivers That Motivate Cloud Migrations
8 Business Drivers that Motivate Cloud Migrations Why do today's businesses migrate to the cloud? At...

Big Data for Finance
Across industries, data continues to grow as an extremely valuable resource. This is especially true...

Connected cities and places
Improving digital infrastructure is key to enabling a smarter city or place to develop, thereby creating...
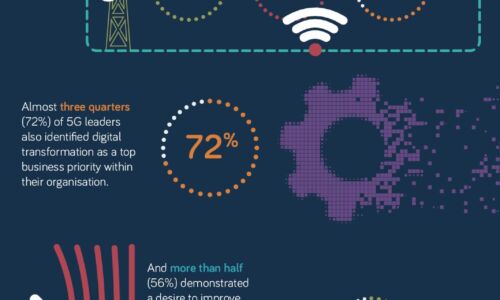
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

Digital Transformation & Risk for dummies
Digital transformation is a critical priority for many companies across most industries, and it's more...

BlackBerry Cyber Suite
The challenge of securing and protecting data and endpoints is not a new requirement, but today it is...

Transform your business with machine learning
8 stories of machine learning success By providing the broadest and most complete set of machine learning...

Redefining Healthcare in the Cloud
Helping you visualise clinical healthcare innovation, and the future of personalised experiences in the...

What Makes Real Threat Intelligence
First popularized in terminology several years ago, threat intelligence means many things to many people....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





