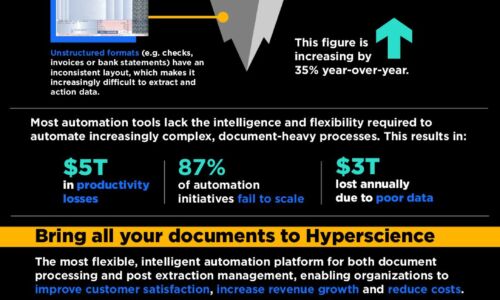
Internet of Things (IoT)

How To Choose a Managed Extended Detection and Response Solution
Organizations face major cybersecurity hurdles. The first challenge is finding effective cybersecurity...
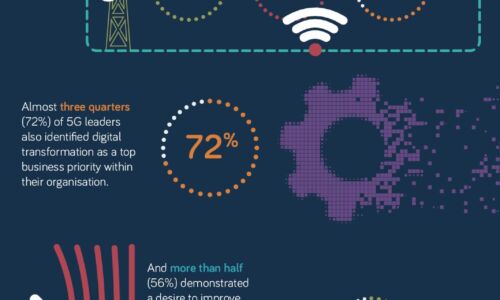
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

Transform your business with machine learning
8 stories of machine learning success By providing the broadest and most complete set of machine learning...

The CISO’s Guide to Effective Zero-trust Access
Best practices in network access stipulate a zero-trust access (ZTA) approach. CISOs looking to implement...

Big Data for Finance
Across industries, data continues to grow as an extremely valuable resource. This is especially true...

Zero Trust Maturity Guide
This guide is designed to help you find quick wins in your zero trust journey and continue making progress...

Empowering Medical Manufacturers to Become Leaders
Due to increasing technology and product complexity, regulatory requirements and supply chain issues,...

Implementing the NIST Zero Trust Architecture with Zscaler
The National Institute of Standards and Technology (NIST) has defined the core components of zero trust...

How to Tackle Ransomware by Managing Human Risk
CybSafe's analysis of ICO data finds the number of incidents of ransomware reported has doubled in a...

3 technologies you need to future-proof your organization
New technology can be a scary thing. New processes to learn, new systems to teach your team and new ways...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.