BYOD

The Digital Workspace: Three Elements of Success
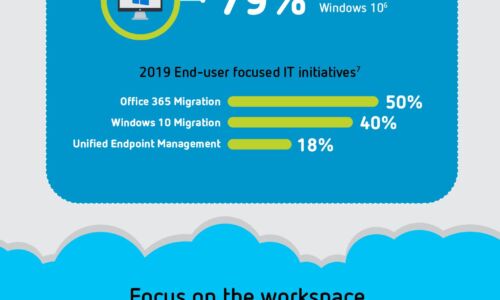
IT leaders say they are actively pursuing digital workspace strategies but still need to overcome some...

Zero-Trust is the Outcome of Identity-Based Access Control
As the IT landscape evolves, new and more sophisticated cybersecurity threats continue to appear. These...

The Evolving Workplace: Everything as a Service
Innovations in technology disrupt traditional business models. One way companies are already starting...

How to Leverage O365 for a Zero Trust Strategy
Enterprise adoption of Microsoft Office 365 (O365) skyrocketed to over 258,000,000 users in 2020 and...

Fleet ELD mandate
With the ELD mandate in effect, companies with vehicles requiring fleets that use paper logs to track...

The Complete Guide to Cloud Economics
Improve decision-making, avoid risk, reduce costs and accelerate cloud adoption. There are two leading...

Future-Ready Identity and Access Management
This e-book offers five fundamentals to help you find a new approach to identity access and management...

On the Agenda: The Year Ahead in Digital Transformation
Wondering how to make the journey to the cloud easier? IDG discusses how Citrix and Microsoft's joint...

Expose the Uncertainty: Best practice for reporting risk
With cyber threats increasing, it's vital for business leaders to understand and mitigate risks that...

Maximizing your Sitecore Investment with Rackspace and Azure
Creating customers for life. In the age of the customer, your online visitors expect an engaging, personalized...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.