BYOD

Making the Grade: End-to-End Security in Education
While students are preoccupied with completing online school assignments and streaming educational videos,...

Unified Endpoint Management (UEM): Address 3 Common Challenges
With digital transformation comes mobile devices, apps and high-speed connectivity that make it possible...
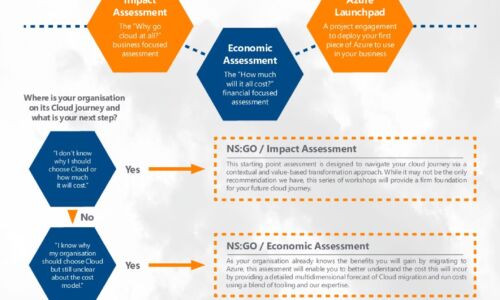
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

High performance with distributed caching
For many web, mobile, and IoT applications that run in clustered or cloud environments, distributed caching...

Forrester: The Balanced Security Imperative
Balanced security requires firms to transition from treating privacy and data security as compliance...

Not All End User Experience Monitoring Solutions Are Created Equal
Digitization has undoubtedly changed the way companies do business with their customers, partners and...

Data In, Value Out
In today's increasingly data-driven business landscape, the companies who succeed are typically those...

Effieciency, Productivity and Growth - Quickbooks Vs NetSuite
Why stay with software that holds your business back when you could use a system that empowers your business? Improve...
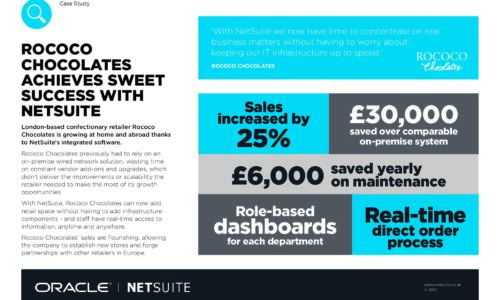
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

The Essential Guide to Intelligent Storage for Virtual Desktops
Organizations of all types and sizes are turning to virtual desktop infrastructure (VDI) and the latest...

The World is Your Workplace: Public Safety Mobile Solutions
Public safety personnel of all types rely on mobile technology to remain connected, efficient and informed....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







