Latest Whitepapers

7 Experts on Moving to a Cloud-based Endpoint Security Platform
Without a doubt, endpoint security has become an urgent priority for many organizations, and it's not...

Achieving transformative business results with machine learning
By providing the broadest and most complete set of machine learning (ML) services, AWS is able to meet...

Unmasking BEC and EAC
Whether they result in fraudulent wire transfers, misdirected payments, diverted payrolls, supply-chain...

Report Summary: TLS 1.3 Adoption in the Enterprise
This research project sought to gauge awareness of and adoption plans for the new TLS 1.3 specification...

The Total Economic Impact Of PayPal's Enterprise Payment Solutions
PayPal's enterprise solutions deliver enterprise-level credit card and alternative payment processing...

Transforming Compliance With Revolutionary Technology
With millions of emails, phone calls, and instant messages sent every day, it's impossible for financial...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...

End-point Log management
Deploying a robust log management solution on end-points can be challenging. Monitoring remote end-points...

Driving Real Behaviour Change
Today's most potent cyber threat isn't a zero-day vulnerability, new malware or the latest exploit kit....

The World is Your Workplace: Public Safety Mobile Solutions
Public safety personnel of all types rely on mobile technology to remain connected, efficient and informed....

Struggling To Securely Keep Up With Digital Acceleration
In today's digital economy, businesses must move fast, rapidly adapting to changes. Increasingly, this...
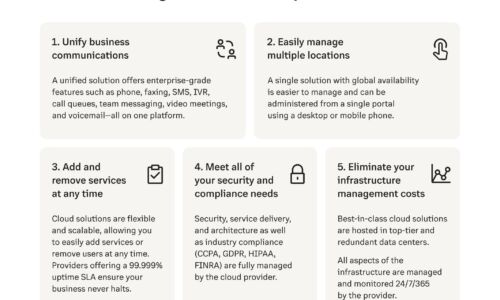
7 Reasons to Switch your On-Premises PBX to the Cloud
Businesses going remote or hybrid require more than what an on-premises PBX can provide. With a cloud...

Digital Marketing Transformed: The future of content
Digital marketing is, by its very nature, a dynamic place to be. We've seen an explosion in the amount...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






