Storage

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

The New Retail Model: A Four-Step Guide to True Algorithmic Retailing
There is one thing successful retailers have in common, particularly in these uncertain times: a firm...

Sophos 2022 Threat Report
Interrelated threats target an interdependent world. We believe that shifting the timescale of attack...

Data-Empowered Construction
In today's construction industry, data analytics is essential for maximizing performance and staying...

Oracle Cloud@Customer Brings Full Cloud Experience On-Premises
Oracle Autonomous Database on Exadata Cloud@Customer and Dedicated Region Cloud@Customer powered by 2nd...

Ten Ways Pure's Flash Solution Can Help You Succeed
Legacy infrastructures are a roadblock to innovation, despite most service providers being heavily reliant...

Unlocking collaboration in higher education
Collaboration and knowledge sharing are pillars of higher education. Instead of working in silos detached...
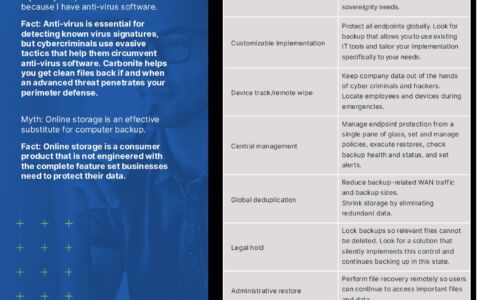
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

THE RISE OF AI AND MACHINE LEARNING
AI has the power to focus the volume of data in financial services. AI and machine learning tools can...

The Total Economic Impact™ Of VMware Workspace ONE for Windows 10
The purpose of this study is to provide readers with a framework to evaluate the potential financial...

Combatting Ransomware by Exposing the Myths
Ransomware continues to pose a credible and costly threat to the enterprise. Misinformation only compounds...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







