Storage

Bring world-class customer experiences and calling into Microsoft Teams
Microsoft 365 is a key platform for employee productivity for organizations everywhere. Those organizations...

Enduring from Home: COVID-19's Impact on Business Security
Faced with shelter-in-place orders in their home counties and states, countless companies transitioned...

The Definitive Guide to Sharepoint Migration Planning
If I've learned anything in more than a decade of working with SharePoint, it's that migration is more...

How 3 Leading Companies Found Peace of Mind with Disaster Recovery
Many traditional DR solutions are unreliable, complex and expensive, requiring significant and time-consuming...

THE RISE OF AI AND MACHINE LEARNING
AI has the power to focus the volume of data in financial services. AI and machine learning tools can...

Cloud Data Security 2023 Report by ESG, a division of TechTarget
…More than half (59%) of respondents believe that more than 30% of their organization's sensitive data...

Protecting Data Capital in your Organization
The digital era is changing the way that organizations think about, protect, and monetize data. Now more...
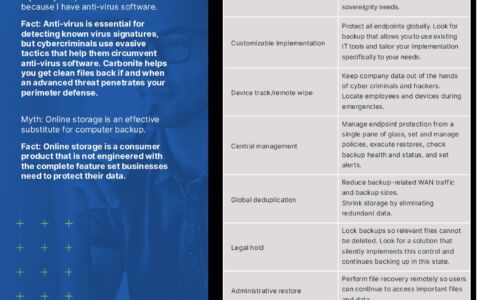
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

Build better endpoint security to protect your entire network
The threat of a serious cyberattack is nothing new — but the situation just keeps getting more complex....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









