Software

The Ultimate Guide to Document Processing Automation
Today, there are many different technologies a line of business department or automation COE are able...

4 Low-Code Best Practices for SAP Fiori Apps
It has been proven that enterprise IT teams that include a no-code/low-code approach for their SAP app...

Ponemon Cost of Insider Threats Report 2022
External attackers aren't the only threats modern organisations need to consider in their cybersecurity...

Building the Business Case for Improving Endpoint Security
As a security provider, we understand that convincing executives to make changes to their stack can be...

How to Accelerate Container Adoption
Developing applications with containers has become an increasingly popular way to operationalise speed,...
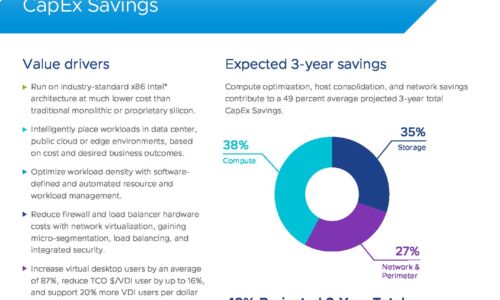
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

EMA Report: Availability and Buying Options in the Emerging SASE Market
Cloudflare One reviewed as a leading provider of Secure Access Service Edge Gartner's Secure Access Service...

Lessons from past vulnerability exploits and how WAF can help
Fight web attacks in seconds without slowing down your website. The onset of 2020 was marked by the disclosure...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






