Operating System

Infrastructure Monitoring 101
For any sized company, the rapidly expanding implementation of today's technology creates unique and...

Securely Work From Anywhere With the Fortinet Security Fabric
The way people work has fundamentally evolved, and organizations need to be able to keep workers productive...

Long-Term Data Retention with Veritas NetBackup
This white paper provides a technical overview of cloud storage as a long-term retention storage solution...

10 Hidden Costs of an On-Premises Phone System (PBX)
Many on-premise phone system (PBX) manufacturers claim that the five-year costs of their systems are...

Cybersecurity For Dummies
Advanced threats have changed the world of enterprise security and how organizations are attacked. These...
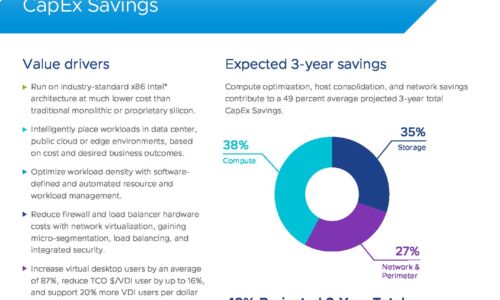
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

What Makes Real Threat Intelligence
First popularized in terminology several years ago, threat intelligence means many things to many people....

Internal Firewalls for Dummies Guide
Organizations can no longer rely on edge firewalls alone to provide network security. Once attackers...

5 Things You Might Not Know About Cloud Security
Many organizations underestimate the security risks of the cloud, often assuming public cloud providers...

TLS Best Practices
The truth is, a simple lapsed certificate can become a time-consuming headache. Unfortunately, 60% of...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








