Network Infrastructure
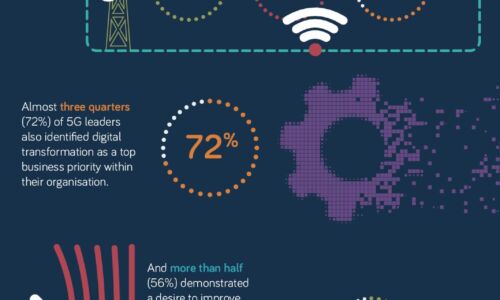
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

DDoS Threat Landscape Report: DDoS Trends from Q3 2022
DDoS attacks are growing larger, stronger, and more sophisticated. In Q3'22, we observed a resurgence...

Guide to Transform Your Network with Advanced Load Balancing
To evolve with the times and deliver capacity to the business, network ops teams are transforming the...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

Isolated Castles: Incident Response in the New Work From Home Economy
Since the shift to work from home, there's been a paradigm shift in the IT and security industry. The...

Threat Spotlight: Protecting your business in 2022
Cybersecurity threats are rapidly evolving. In the latest attacks, cybercriminals are using a range of...

IDC Whitepaper: Achieving Network Modernization for the Decade Ahead
Every organization is now defined by the digital services it delivers. From engaging customers with new...

Report: ICS/OT Cybersecurity 2021 Year in Review
Dragos is excited to present the fifth year of the annual Dragos Year In Review report on Industrial...

Deliver secure, immersive gaming experiences with Cloudflare
Between growing their communities, meeting player expectations and defending against attacks, gaming...

GigaOm Radar for DDoS Protection
Cloudflare ranked higher than any other assessed vendor and is named a 'Leader' and 'Fast-mover'' in...

Struggling To Securely Keep Up With Digital Acceleration
In today's digital economy, businesses must move fast, rapidly adapting to changes. Increasingly, this...

Common Browser Isolation challenges, and how to overcome them
A growing number of security teams are implementing a Zero Trust security strategy, in which no application,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






