IT Management
Ten predictions for the next decade of analytics
AI and other analytics technologies are driving incredible innovations and advancements that are making...

Change management blueprint for contact centre digital transformation
The COVID-19 pandemic put organisational change into hyperdrive. Businesses were compelled to move to...

Safeguard Your Infrastructure from Ransomware and Cyber Threats
Data, the new currency of the global economy, has become the single most valuable asset for a majority...

Operationalizing Multi-Cloud: Four Success Stories
Now more than ever, organizations are leaning on the public cloud to drive innovation with speed and...
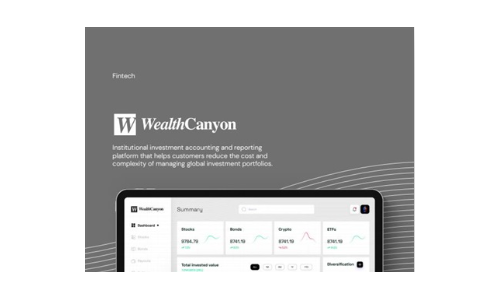
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...

Harden Your Defenses With Security Analytics
Analyze data in real time with the right SIEM approach. It's time to step up your security game. If you...

CISO Guide: Securing Cloud Communication and Collaboration
With UCaaS platforms accelerating innovation and sharing in productivity resources like chat, voice,...

Moving Your Databases To The Cloud
Are you thinking about moving your Oracle databases to the cloud or making the transition to Database...

SteelCentral Aternity for Microsoft Apps and Devices
End User Experience Monitoring for troubleshooting and validating change for Office, Windows, and Surface...

The CIO's Guide to Transformation with AppExchange
A huge part of a CIO's role is 'keeping the lights on'. They are responsible for making sure systems...

Successfully innovate with AI and ML
Rise above the barriers of implementation Organizations across industries and geographies have long realized...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







