Endpoint Security

A Buyer’s Guide to Optimizing Remote Employees’ Extended Network
The shelter-in-place mandates put in place earlier in 2020 sent most employees home, and for the next...

Top 10 Best Practices for vSphere Backups
More and more companies come to understand that server virtualization is the way for modern data safety....

Elastic Cloud Gateways: The Evolution of Secure Cloud Access
Enterprise security groups today face a daunting task. While their core responsibility of protecting...

Ransomware Prevention Is Possible
Ransomware is a form of malware that encrypts files to prevent victims from accessing their systems and...

Moving Endpoint Security to Predictive Cloud
Endpoint security is broken. Traditional antivirus (AV) vendors aren't keeping up with today's threats....

10 Endpoint Security Problems Solved By The Cloud Infrographic
The three challenges you're likely facing – cost and complexity, defenses that can't keep up, and overburdened...

How to Stop Ransomware Attacks
This ebook How to Stop Ransomware Attacks provides in-depth guidance for quickly setting up stronger...

Incident Response Use Cases
According to an IBM study, the vast majority of organisations surveyed are unprepared to respond effectively...

Consolidate Cybersecurity Vendors to Accelerate Detection and Response
Organizations of all shapes and sizes are increasingly embracing digital transformation, cloud-delivered...

Threat Spotlight: Protecting your business in 2022
Cybersecurity threats are rapidly evolving. In the latest attacks, cybercriminals are using a range of...

Hidden Costs of Endpoint Security
When it comes to endpoint security, CISOs are in a bind. Most assume that endpoints will be compromised...
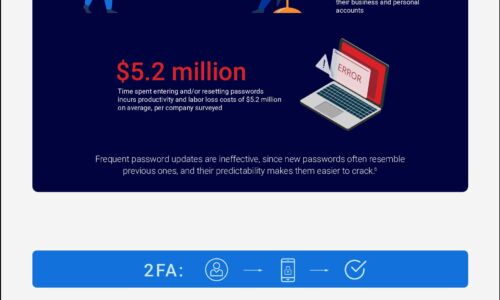
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






