Desktop/Laptop OS

Organizations Accelerating Their Digital Workplace Achieve Improvements
This study sought to understand whether, and to what degree, an organization's adoption of modern device...

Moving Forward in a Work-from- Anywhere World
Welcome to The Gorilla Guide To…® Moving Forward in a Work-from-Anywhere World, Foundation Edition....

Security Strategy Checklist
This self-assessment is designed to help you evaluate the security risks in your environment. It is intended...

SD-WAN Benchmarking Best Practices for QoS by The Tolly Group
While Internet bandwidth increases continually for remote sites, the application demand for that bandwidth...

Quest® KACE® SMA reduces software license compliance stress
Do you know whether all your software licenses are compliant? Your IT landscape has gotten more and more...

MITRE Engenuity™ ATTandCK® Evaluation
MITRE has become the common language of EDR and is the de facto way to evaluate a product's ability to...

E-signatures for Global Businesses
This eBook covers the benefits and challenges of electronic and digital signatures, compliance considerations,...

Use Case - Optimizing SIEM
Security Information and Event Management (SIEM) solutions form the core of many organizations' security...
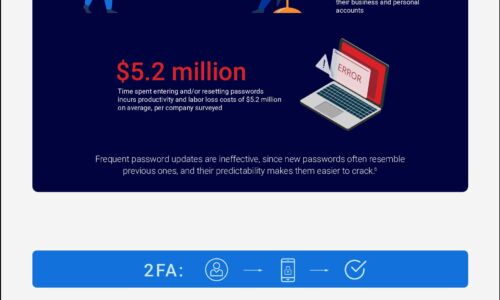
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Windows 10 for Dummies, 2nd Edition (Full eBook)
The most comprehensive guide to Windows 10, updated with the latest enhancements. This eBook includes...

AI-Augmented HPC From Dell Drivers Customer Successes
Science and engineering rarely stand still. Once one problem is solved, it unlocks the approach to a...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







