BYOD
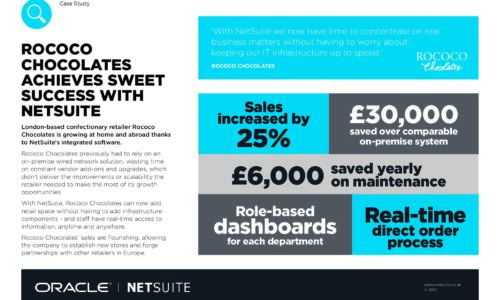
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

The Beginner's Guide to Dynamic Case Management
What is dynamic case management? Who is using it and how can it help you prepare for the future of work? The...

Zero-Trust is the Outcome of Identity-Based Access Control
As the IT landscape evolves, new and more sophisticated cybersecurity threats continue to appear. These...

Enabling Great Customer Experience
The blueprint for success starts with a technologyfoundation that links an organisation's front- and...

App Development as a Core Business Capability
Many organisations now understand the critical role that apps play in enabling their people, as well...

How Effective Retailers Balance Customer Engagement and PCI Compliance
For CIOs of retail organizations, compliance with Payment Card Industry (PCI) standards is a top concern,...

Expose the Uncertainty: Best practice for reporting risk
With cyber threats increasing, it's vital for business leaders to understand and mitigate risks that...

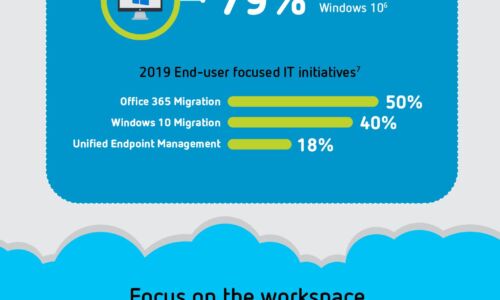
The definitive guide to Citrix Workspace
User experience and productivity. Use this guide to understand why Citrix Workspace delivers the solution...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.