Virtualization

Achieving pervasive security above, within and below the OS
It seems that every few months, another prominent global brand experiences a major security breach and...

SASE-Ready WAN Edge for the Work from Anywhere Era
Enterprise networks are on the verge of a major tipping point, driven by the shift from employees working...

A Guide to Assessing Security Maturity
Cybersecurity is an unavoidable part of daily business operations for organizations of all sizes and...

3 Ways Emotional Connections Can Power CX
When personalization isn't paying off and data doesn't help you make sound decisions, it's time to renew...
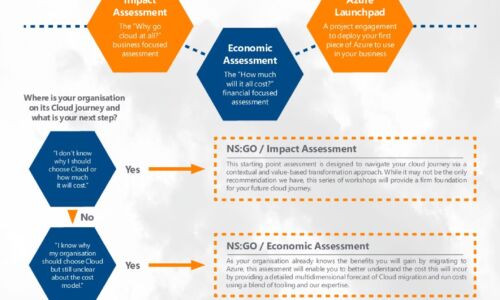
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

Enterprise Backup and Recovery Made Easy
Protecting enterprise data in a complex IT environment is challenging, time-consuming, cumbersome and...

Windows Virtual Desktop Jumpstart
Not all applications are web-based or designed to run from the cloud. Many applications still require...

Penetration Testing For Dummies
Target, test, analyze, and report on security vulnerabilities with pen-testing Pen-Testing is necessary...

How to Increase Agility with Hybrid Cloud Automation
As organizations innovate faster than ever, they bring new applications and services to market in more...

Data-Driven Transformation in Europe
Although governments across Europe may differ in their ideologies, statutes and constitution – there...

The Top 10 Reasons to Upgrade to VMware vSphere 7
Customers today demand rapid delivery of innovative applications. To meet those demands, businesses must...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







