Security Management

The Forrester Wave™: Privileged Identity Management
in our 35-criterion evaluation of privileged identity management (PiM) providers, we identified the 11...

BIOS Security – The Next Frontier for Endpoint Protection
Everyone is familiar with the process of booting up a computer. Many of us do this every day — pressing...

Ransomware Survival Guide
Be Ready for Ransomware Ransomware is an old threat that just won't go away. While overall volumes have...

3 steps to transforming security operations
With cyber breaches ever-rising in cost and frequency, you need to build more effective, collaborative...

5 Steps Toward Cybersecurity Resilience for Government Agencies
Cybersecurity attacks continue to grow in number, in complexity and in impact. State and local government...

Cloud Security Automation For Dummies®
Get the big picture on cloud security, in all its complexity, speed, and scale. Our Cloud Security Automation...

What Today's Retailers Need in a Security Architecture
Retail cybersecurity in the age of the omnichannel customer experience requires CIOs and vice presidents...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

10 Endpoint Security Problems Solved By The Cloud Infrographic
The three challenges you're likely facing – cost and complexity, defenses that can't keep up, and overburdened...
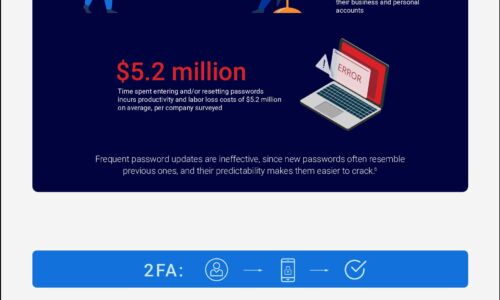
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Deploying Consistent Application Services in Multi-Cloud Environments
Most organizations prioritize cloud flexibility—and let application teams choose the best environment...

Addressing the Top 10 Security Issues Organizations Face
Cybersecurity must be a top-level priority for any organization and for many it is. Security should be...

BlackBerry Cyber Suite
The challenge of securing and protecting data and endpoints is not a new requirement, but today it is...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





