Network

Healthcare IoT, the RX for Providers and Patients
Healthcare providers have a lot on their plates. Costs are always on the rise, and staff shortages put...

User Risk Report
Your cybersecurity posture is only as strong as its weakest link. And in today's people-centric threat...

You Got Phished, Now What?
Security leaders work hard to prevent successful phishing attacks. But, despite email security solutions...
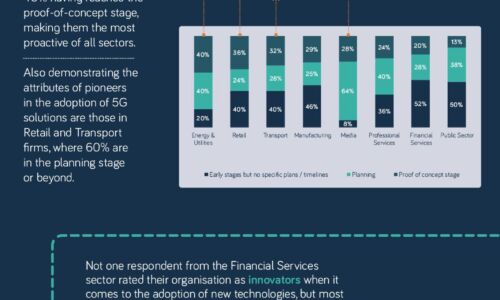
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Deliver agility with an expanded vision for SandOP
Though sales and operations planning (SandOP) originally aspired to bring business functions together...

How to Deploy a Comprehensive DevSecOps Solution
Securing DevOps is a complex undertaking, DevOps tools grow and change at a fast pace. Containers and...

Achieving pervasive security above, within and below the OS
It seems that every few months, another prominent global brand experiences a major security breach and...

2021 Thales Cloud Security Study
The pandemic has pushed organisations into many changes in the last year but the move to greater use...

Forrester A Practical Guide To A Zero Trust Implementation
Secure Workload Access On Your Journey To Zero Trust Including the licensed Forrester report: A Practical...

NIST Cybersecurity Framework
The document gives you an overview of the NIST Cybersecurity framework, an internationally widespread...

Ransomware Protection Checklist
Ransomware attackers are increasingly employing more sophisticated attacks and defeating existing defenses....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







