Network

Cloud Computing for Dummies
Cloud computing is a topic that technology pros need to know to stay ahead of the computing game. Cloud...

Reduce data processing time by up to 50%
As the world around us becomes more digitised, data is becoming more and more important. The problem?...

Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Making all the Right Connections
Using digital workflows to blast through barriers, drive loyalty, and accelerate growth. Organizations...

The Inner Circle Guide to Agent Engagement and Empowerment
Your agents aren't going to ask you for more automated tools, empowered and personalized coaching, and...
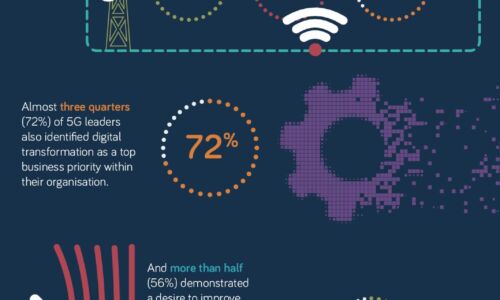
What makes a 5G Leader?
With 5G a still nascent technology, opportunity remains for businesses to accelerate adoption of this...

Debunking the Top 5 Myths About Malicious Bots
Today, as much as 40% of all Internet traffic consists of bots: non-human users that perform automated...

Nasuni for Rapid Ransomware Recovery
The FBI's Cyber Crime division defines ransomware as 'an insidious type of malware that encrypts, or...

Escape the Ransomware Maze
Ransomware is an ever-evolving form of malware designed to steal business-critical data and then sell...

Which WAF is right for me eBook
Despite the tech industry's collective best efforts to bolster secure application development practices,...

Supercharge your digital workspace
Delivering a great user experience is everything. You already know the advantages of secure digital workspaces...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







