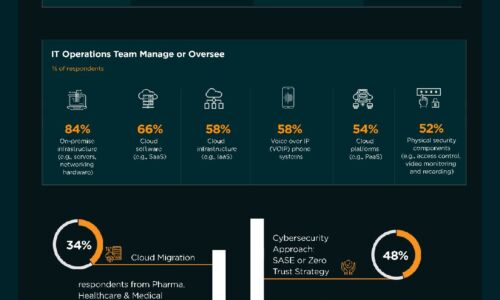
Mobile Security

Forrester Wave, We're a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

Top 10 Best Practices for vSphere Backups
More and more companies come to understand that server virtualization is the way for modern data safety....

7 Experts on Moving to a Cloud-based Endpoint Security Platform
Without a doubt, endpoint security has become an urgent priority for many organizations, and it's not...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Forrester Wave, We’re a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...

Why Corelight Is Your Best Next Move In Enterprise Security.
Despite spending billions annually on security infrastructure and services, even the most sophisticated...

Slack is Custom-Built for Enterprise Companies
Over the past few weeks, we've all been challenged to rethink how our teams work together. We've had...

Top 5 Ways to Simplify Data Protection with Microsoft Azure
Read this white paper to find out five ways that you can simplify data protection with Microsoft Azure,...

Centralised Control Simplifies Management, Boosts Security
Aquila Heywood wanted to update its privileged access management processes to increase data security...

Hidden Costs of Endpoint Security
When it comes to endpoint security, CISOs are in a bind. Most assume that endpoints will be compromised...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.