Machine Learning

The Mimecast-Netskope-CrowdStrike Triple Play
Security and IT organizations must protect against new attacks at scale — and safeguard data in use,...
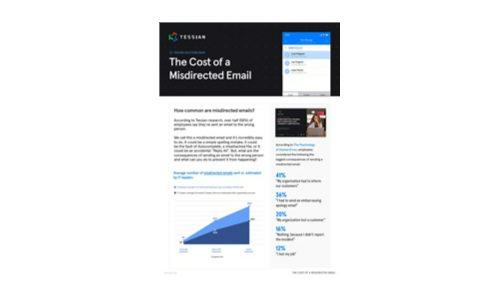
What is the Cost of a Misdirected Email?
The average number of misdirected emails is almost always higher than IT leaders estimate, making it...

5 Benefits of Partnering with Webroot
While cyberattacks continue to evolve in volume, organization, and sophistication, security technology...

Simplify the complexity of data management
Every aspect of a business produces and requires information whether it's marketing or human resources....

How to Leverage O365 for a Zero Trust Strategy
Enterprise adoption of Microsoft Office 365 (O365) skyrocketed to over 258,000,000 users in 2020 and...

Protecting Your Hybrid and Hyperscale Data Centers
Organizations are building hybrid data centers that consist of composable and scalable architectures....

Brute Force: Guide to Mitigating Attacks
A brute force attack is when an attacker attempts to gain access to an environment by identifying valid...

Protect your organization from ransomware
Get a glimpse of the criminal players who operate within the underground ransomware economy. We'll help...

How to secure your business with the Content Cloud
Hope is NOT a strategy: Secure your business with the Content Cloud Seems like every week there's news...

Flexible for the future
IT decision makers are tackling a major challenge: how can we architect our IT in a way to maximise access...

Ensuring compliant communications in Financial Services
The pandemic has reshaped business in myriad ways, none so much as how people communicate. In a few months,...

Ignite Your Innovation Engine
Dell Technologies believes that the engine you use to drive your business forward should be designed...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






