ERP

CISO’s Guide to Choosing an Automated Security Questionnaire Platform
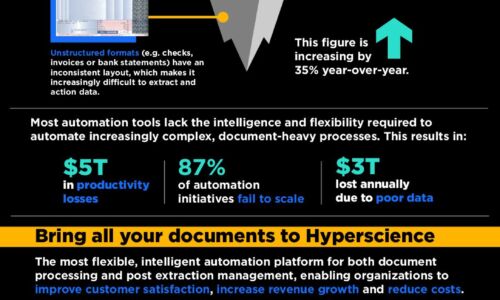
Failing to adequately screen suppliers' security can lead to data breaches, which can shut down operations,...

97% of data sits unused by organisations
Data has the capability to transform your business, but only if it's collected and processed in the right...

Business in the new economy landscape
How we coped with 2020 and looking ahead to a brighter 2021: The state of European midsized businesses. Medium-sized...

The CISO's Guide to Ransomware Prevention
Ransomware attacks have transformed the cyber attack landscape. These sophisticated and persistent threats...

Lay the Foundation for Zero Trust
Zero Trust has been a topic of discussion in the Federal Government for some time. However, the approach...

The Cybersecurity fail-safe: Converged Endpoint Management (XEM)
Organisations are experiencing more attacks than ever before. Cybersecurity Ventures expects a ransomware...

Workforce Management in Multiservice Organisations
How to create a more effective approach in the service and facilities management industries. Siloed operations...

Lessons from REvil's Return
Ransomware is not just another buzzword. It is a very real threat to businesses and educational institutions...

How a Modern Payments Set Up Can Help You Unlock Revenue
Payments in 2022 are much different than they were just a few short years ago. From Boomers to Gen Z,...

4 steps to manage risk and resilience in real time
Here's your roadmap to embedding risk management across the enterprise and removing silos so people and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.