Embedded Systems

PHP, MySQL, and JavaScript All-in-One For Dummies
Get the basics on four key web programming tools in one great book! PHP, JavaScript, and HTML5 are essential...

Windows 10 for Dummies, 2nd Edition (Full eBook)
The most comprehensive guide to Windows 10, updated with the latest enhancements. This eBook includes...

The New Reality: Bring Order To Chaos With Unified Endpoint Security
Chaos and confusion dominated the enterprise cybersecurity landscape even before the COVID-19 pandemic...

BlackBerry Cyber Suite
The challenge of securing and protecting data and endpoints is not a new requirement, but today it is...

Veeam + Microsoft Combine to Offer Rapid Time to Value
IT leaders are discovering that default data protection schemes are not as robust as they desire. As...

BlackBerry Guard: Solution Brief
Many businesses overlook or underinvest in managed detection and response (MDR), a critical aspect of...

Learning SQL: Generate, Manipulate, and Retrieve Data
As data floods into your company, you need to put it to work right away—and SQL is the best tool for...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...
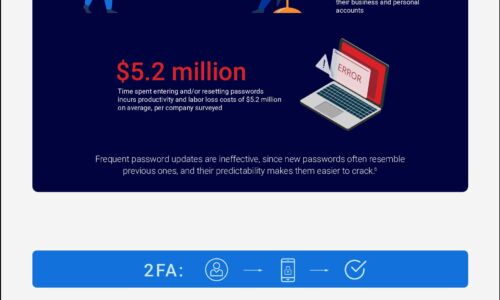
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








