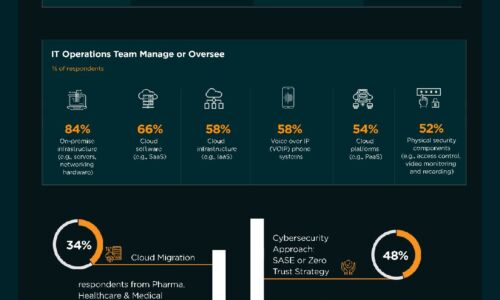
Data Recovery

Best Practice Makes Perfect: Malware Response in The New Normal
Before Covid-19, cyber security teams already confessed to being overworked – as high-profile security...

The Case for Secure Communications
The tapping of voice communications has occurred virtually as long as electronic communication has been...

Cyber Attack Trends: Check Point’s 2022 Mid-Year Report
The war in Ukraine has dominated the headlines in the first half of 2022 and we can only hope that it...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

Transforming Security in the Mobile Cloud Era
In the age of digital transformation, maintaining secure interactions among users, applications, and...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Deploying Consistent Application Services in Multi-Cloud Environments
Most organizations prioritize cloud flexibility—and let application teams choose the best environment...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

Cybersecurity for retail: Prevention is better than the cure
Prevention is almost always better than the cure. But how many organisations are living up to the promise...

Python for Data Science For Dummies, 2nd Edition
The fast and easy way to learn Python programming and statistics Python For Data Science For Dummies...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.