Compliance

Finding a Setting Worthy of Your 'Crown Jewels'
Keep all the Data in a single, unified Database – Oracle Exadata For most companies, data is critical...

5 steps to boost employee productivity and organizational efficiency
Every organization needs to empower employees if they want higher productivity and satisfaction wherever...

Five Ways to Reduce the Cost and Complexity of File Sharing
There are two ways a legacy technology solution gets retired. Gradually, and all of sudden. No one likes...

Fortinet Federal Government Cybersecurity Solutions
U.S. federal agencies operate some of the world's largest and most complex digital networks, but many...

Automating Safety
As the overly-used phrase so correctly states: 'safety is no accident'. Dedication to safety-first culture...

Breaking Down BEC
The Modern CISO's Framework for Identifying, Classifying and Stopping Email Fraud Business email compromise...
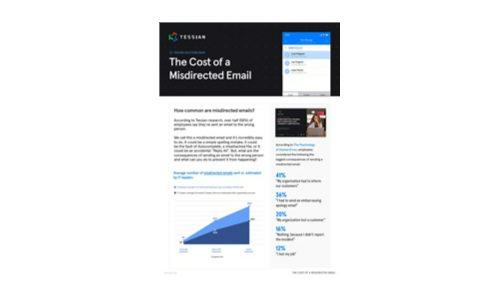
What is the Cost of a Misdirected Email?
The average number of misdirected emails is almost always higher than IT leaders estimate, making it...

Threat Briefing: Supply Chain Attacks
Cyber criminals are getting bolder and more sophisticated with their threats. Supply chain attacks can...

The Forrester Wave™: Big Data NoSQL
In this report, Forrester states that, 'NoSQL has become critical for all businesses to support modern...

Ponemon Cost of Insider Threats Global Report
Independently conducted by Ponemon Institute External attackers aren't the only threats modern organisations...

Four Compliance Trends For 2021
If 2020 was the year the financial services industry was turned on its head, what's in store for compliance...

Learn how to build a business framework designed for data management
The center of a best practice approach must include a complete view into your organization and its technology...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






