Compliance

The AI & Machine Learning Imperative
Companies across various industries are seeking to integrate AI & machine learning (ML) into workflows...

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...

2022 MSP Threat Report
This report was created by the ConnectWise Cyber Research Unit (CRU)—a dedicated team of ConnectWise...

The CIO's Guide to Identity Driven Innovation
Today's CIOs are increasingly accountable for more than just enabling the organisation with tools and...

Sotero Data-In-Use Encryption
Though encryption is the most effective way to reduce the probability of a security breach, traditional...

The 7 Hidden Truths of Cloud Security
Based on extensive, up-to-date knowledge and experience from WithSecure consultants, threat hunters and...

How Proofpoint EFD Is More Than Just DMARC
A raft of solutions have sprung up to help organisations set up and manage their DMARC strategies. Like...

Enabling Great Customer Experience
The blueprint for success starts with a technologyfoundation that links an organisation's front- and...

How to Accelerate Container Adoption
Developing applications with containers has become an increasingly popular way to operationalise speed,...
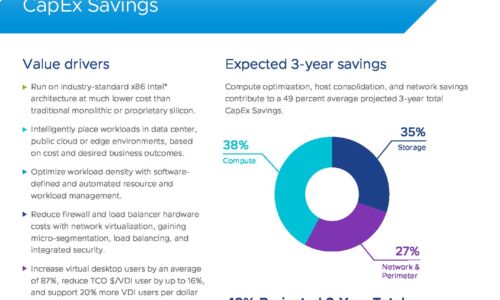
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

The Anatomy of an Insider Threat Investigation
For decades, perimeter-based security strategies have been the starting point for most cybersecurity...

The Cybersecurity fail-safe: Converged Endpoint Management (XEM)
Organisations are experiencing more attacks than ever before. Cybersecurity Ventures expects a ransomware...

Ten Ways to Improve IT Efficiency with an SOE
In today's digital businesses, IT organisations are expected to deliver more services at a faster pace...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





