Compliance

Advanced Application Threats Require and Advanced WAF
The threat landscape is dramatically different than it was just 5 years ago. A traditional web application...

Proofpoint Information and Cloud Security Platform
The Proofpoint Information and Cloud Security platform combines many of our products to address secure...

Five things every business needs to know about GDPR
After years of preparation and drafting, the final t's were crossed and i's dotted on the General Data...

Five Ways to Reduce the Cost and Complexity of File Sharing
There are two ways a legacy technology solution gets retired. Gradually, and all of sudden. No one likes...

Achieve Cloud Security Cost Savings Through SIEM Optimization
Tame Rising SIEM Costs and Complexity Do you worry that your SIEM is falling behind on efficiently handling...

Unified Endpoint Management (UEM): Address 3 Common Challenges
With digital transformation comes mobile devices, apps and high-speed connectivity that make it possible...
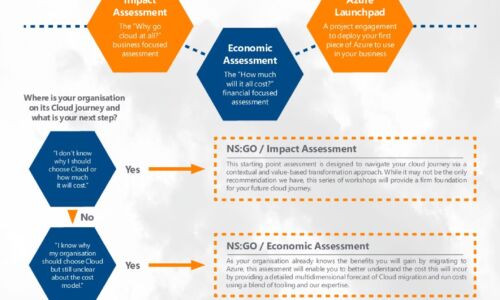
Azure Accelerator kit: Travel in the fast lane with New Signature
At New Signature, we understand that organisations are finding it difficult to start their Public Cloud...

Complete Cloud Security for Legal Firms
Thales have a long history in securing some of the world's most sensitive data, and law firms are increasingly...

Hybrid Work Drives the Need for ZTNA 2.0
The COVID-19 pandemic has had a profound effect on the world. Businesses have compressed into months...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









