Collaboration

Cybersecurity For Dummies
Advanced threats have changed the world of enterprise security and how organizations are attacked. These...

Complete Protection at the Edge Whitepaper
How effective protection at the edge can secure the most critical assets, mitigating threats closest...

Facing the future: Digitization in the Public Sector
The continuous improvement with the capabilities of business technologies – like cloud computing and...

AWS Cloud Operations
Built for operating at cloud scale, AWS Cloud Operations offer a clear and easy path to the business...

Python All-In-One For Dummies
Your one-stop resource on all things Python! Thanks to its flexibility, Python has grown to become one...

From Legacy Infrastructure to the Cloud: A Migration Journey in 5 Steps
Simplify your bank's move to the cloud It takes 8 hours to recreate a lost file, according to TechTarget....

Perimeter Protection and Control The Key to Business Continuity
Critical online services are under constant attack. Only Edge defenses offer adequate protection. As...

3 steps to transforming security operations
With cyber breaches ever-rising in cost and frequency, you need to build more effective, collaborative...
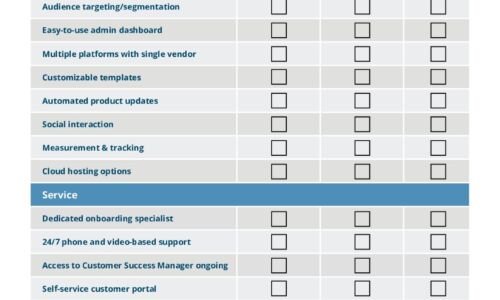
IT Comms Plan Bundle
IT teams need to communicate important messages across their organization – from scheduled maintenance...

The Definitive Guide to Sharepoint Migration Planning
If I've learned anything in more than a decade of working with SharePoint, it's that migration is more...

Strategies for successfully managing privileged accounts
Getting identity and access management (IAM) right for your standard users is hard enough. What about...

5 steps to boost employee productivity and organizational efficiency
Every organization needs to empower employees if they want higher productivity and satisfaction wherever...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






