Cloud

Application Protection Report 2022: In Expectation of Exfiltration
Welcome to F5 Labs' Application Protection Report 2022. As in years past, the goal of this report is...

Take Control of Security Operations with Consolidation and XDR
The constantly evolving cyber threat landscape and steady stream of cybersecurity technologies designed...

Is your SaaS company's billing problem actually a data problem?
Planning a billing platform upgrade? Usage Engine, our purpose-built usage data management software,...

Part Four- Futureproofing your cybersecurity strategy
Email account takeovers are among the most insidious and damaging cyberattacks—used to invade companies...

Book of Knowledge: Employee Experience
Keeping employees engaged, productive, and connected has never been more important—or more difficult....
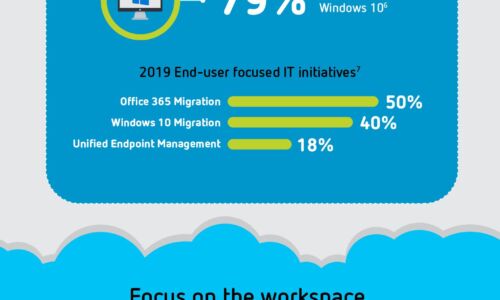
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

Parivartana - The Role of Data and Analytics in Social Transformation
From personalized healthcare to digital farming, and from energy management to digital governance solutions,...

Best-in-class procurement planning 101
Download now to discover how to leverage best-in-class procurement planning to drive process e!ciencies,...
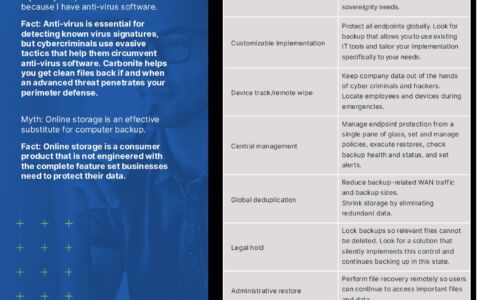
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

A CIO’s guide to creating the workplace of the future
Whether you're looking to retain employees, grow your business or boost your revenue, you've got to stay...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.








