Cloud

Brute Force: Guide to Mitigating Attacks
A brute force attack is when an attacker attempts to gain access to an environment by identifying valid...

User Risk Report 2018
Risky end-user behaviours are impacting organisations around the world, with implications that can be...

Protect your Data and Secure your SQL Server Database Operations
You manage hundreds of SQL Server databases spread over multiple sites and departments, even as you face...

Get Closer in 2021: Key Trends from NRF
Another by-product of 2020 is the digital transformation that is happening within the retail industry....

Smart Data Visualization: How to Design Best-in-Class Dashboards
Create stunning data visualizations that tell a story with your data and highlight the Key Performance...

The Evolution of Cybersecurity
Cybersecurity Through the Years As we look at the ever-increasing, technology-dependent cyber environment...

Oracle Cloud@Customer Brings Full Cloud Experience On-Premises
Oracle Autonomous Database on Exadata Cloud@Customer and Dedicated Region Cloud@Customer powered by 2nd...

Insider’s Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...
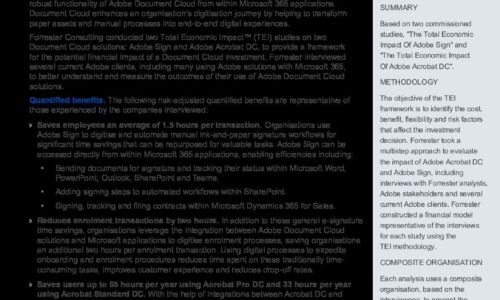
The Total Economic Impact of Adobe Document Cloud & Microsoft Spotlight
Forrester interviewed several current Adobe clients, including many using Adobe solutions with Microsoft...

Fortinet Secures the Intelligent Enterprise Running SAP
Business leaders embrace SAP HANA functionality to stay on top of emerging trends and evolving business...

IDC Tech Spotlight: Employee Experience
A mature employee experience program can simplify workflows across interfaces, online systems, apps,...

Risk-Aware Data Privacy
Organizations around the world are scrambling to address data-privacy challenges amid workplace shifts,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






