Applications

The Human Factor 2021 Report
As the global pandemic upended work and home routines in 2020, cyber attackers pounced. Dive deep into...

Understanding Log Analytics at Scale
The humble machine log has been with us for many technology generations. The data that makes up these...

What the Heck is IAST?
In this eBook, you will learn what IAST is and why it's much different than the previously well-known...

The New Future of Work
To address the challenges of 2020 and emerge stronger in this New Future of Work organisations need to...

4 Low-Code Best Practices for SAP Fiori Apps
It has been proven that enterprise IT teams that include a no-code/low-code approach for their SAP app...
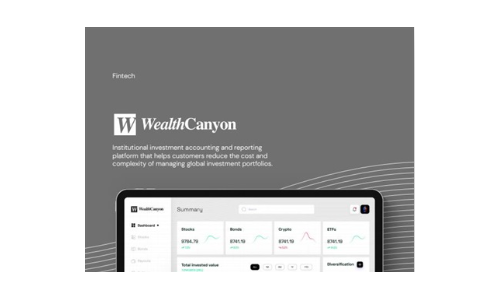
Wealth Canyon
Software companies in the financial industry, such as WealthCanyon, face challenges in collecting and...

Guide to Electronic Signatures
As work evolves to take place outside the four walls of the traditional office, small and midsize organizations...

Cybercrime tactics and techniques
2019 is off to an action-packed start in cybercrime. From a steadfast increase of pervasive Trojans to...

Best Practices in Buying Down Risk
Traditional approaches fall short when attempting to buy down risk in an ever-changing environment. Conflicting...

3 steps to transforming security operations
With cyber breaches ever-rising in cost and frequency, you need to build more effective, collaborative...

The CIO’s Guide to Data and Analytics Innovation
Discover how Workday enables businesses to make faster, better decisions with one source for all your...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






