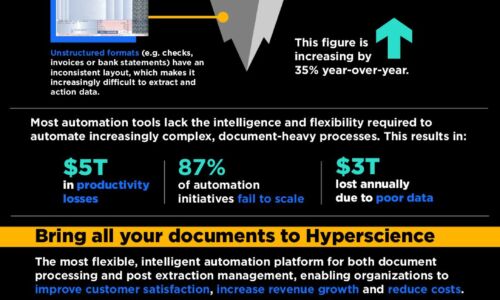
AIM

Cultivating a future-proof customer journey strategy
When the pandemic forced a seemingly overnight exodus from in-person to online, consumers and businesses...

How to Help Prevent Increasingly Rampant Brand Exploitation
Brands have been the unwitting victims of scams since time immemorial. Now, in the age of phishing, it's...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

CIO Roadmap to Hybrid and Multi-Cloud
While cloud has become a key driver of business expansion and operational efficiency, business and IT...

Getting Faster: Know Your Website, and Know What's Slowing It Down
Speed and performance of your website significantly impact revenue growth and conversions. The numbers...
Cultflicks
CULTflicks is a niche video streaming entertainment company that offers the unique experience of specialized...
13 Email Threat Types To Know About Right Now
Traditional email security doesn't cut it anymore. In today's rapidly evolving environment, traditional...

Sophos 2022 Threat Report
Interrelated threats target an interdependent world. We believe that shifting the timescale of attack...

The Human Factor 2021 Report
As the global pandemic upended work and home routines in 2020, cyber attackers pounced. Dive deep into...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.